If in the past we have repeatedly stressed that the government and enterprise users should be prepared in the field of Internet security, here the so-called "security" is the user has not encountered major security incidents, or have been attacked or attack but they can make nothing of it then the recent "Ling mirror, incident no doubt to the world of Internet information security alarm.
In March this year, South Korea suffered severe APT network attack, South Korean broadcasting company, cultural radio, television and other media, Yonhap Shinhan bank, Agricultural Bank and other financial institutions of the computer network that paralyzed. The attack is characterized by hackers using antivirus software patches, trust relationships between servers and other terminals, and malicious programs that cause disastrous results. From this event, Symantec AntiVirus software is not operation on the server security audit, is the main reason for the accident. Because of the strong APT attack, its attack mode has changed greatly compared with the traditional attack mode. The traditional anti-virus and intrusion detection systems are more inclined to monitor, and how to adopt new security strategies to cope with changing attacks, and we must rethink and perfect our next generation security system.
The advent of the big data era, in the security field, information systems planning, construction, investment and other decisions will increasingly be based on data and analysis to make judgments, rather than the past based on experience and intuition model. How to collect and analyze data, provide statistical reports regularly, including the type of attack, attack high risk distribution statistics, security vulnerability issue, how to directly show the real-time security situation, information systems provide data basis for safety decision-making has become the most important issue facing the government and enterprise users.
We suggest that users of government and enterprises should solve the problem of information system security from the following four aspects:
In order to solve user problems encountered in the security operation, Topsec quanyun service using an Topsec service management system cloud service center technology platform, advanced experience and mature security operations team, relying on the national regulatory authority from the analysis of data, provide convenient and efficient secure cloud services, for enterprise units include: 7*24 hour remote security monitoring, security monitoring, security audit, security incident response, security consulting, periodic safety inspection, maintenance and other services in the local field, can help users quickly and effectively solve the security problem, effectively alleviate the users in the security system facing the operation and maintenance phase of work pressure, improve the running effect of the enterprise information security system.
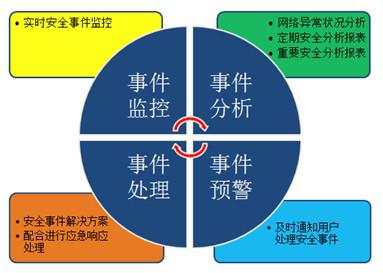
As the first commercial domestic security service organization, talent service center with quanyun provide security experience for users of information system in the Beijing Olympic Games, Shanghai, World Expo, the Guangzhou Asian Games, eighteen, NPC and CPPCC important period, relying on talent of anti Laboratory (alpha -Lab) emergency treatment on opinion mining security vulnerabilities and the major security vulnerabilities, and through the experience of many years of accumulation, the feedback control to the platform to the platform, according to the feedback results through the intelligent learning to update its monitoring mechanism, establish security knowledge sharing, in order to achieve the purpose of closed-loop. Through cloud security services to help users establish monitoring, analysis, early warning and handling of the operation and maintenance mechanism, combined with inspection and emergency response, to achieve one-stop security hosting.







