Data Protection Solutions for a University
Solutions for Data Protection at XXX University of Science and Technology
Requirement Analysis
XXX University of science and technology is a typical physical and virtual hybrid environment. At the same time, there are many applications in the University, and both data and applications need to be protected. However, XXX University of science and technology has encountered many problems and challenges in choosing the right solution, as follows:
· Too much application system leads to excessive load of common data protection products
Educational system, OA, website groups, teaching platforms and other applications on the system requires a complete set of data protection program. In addition to being able to form recoverable data copies, the program should also provide automated protection processes, from protection to final recovery, and minimize the degree of manual intervention, with high manageability.
· The application system will provide classified protection according to the importance level and the data protection products
The core application system should have the ability of disaster tolerance. When the application system is accidentally interrupted due to an accident, there is a corresponding disaster tolerant server to continue to provide service to the outside world.
· The "physical + virtual" environment is complex and requires data protection products to provide a unified solution
The data protection scheme should be able to provide a unified protection for the user's hybrid environment, rather than deploying multiple scenarios within the IT environment.
· A large number of machines, the need for a unified, simple operation and maintenance management to improve efficiency
Conceptual Design
Taking into account the current application of XXX University of science and technology, as well as the actual investment situation, and ultimately adopt the integrated disaster recovery program, the program deploys TxCloud to protect the user's data locally. The scheme topology is as follows:
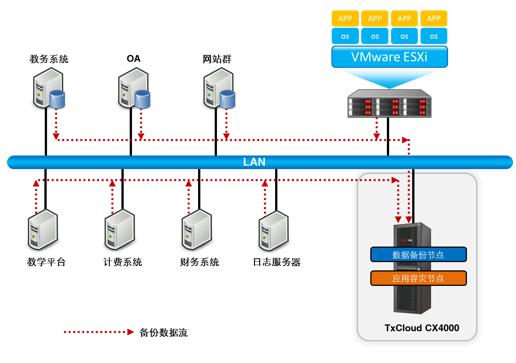
图 1 XXX科技大学数据保护解决方案
Scheme effect
According to the above framework to deploy integrated backup disaster recovery program, the program effect is as follows:
· Deal with many applications, no load pressure
TxCloud multi node feature can load the pressure and the network pressure of data transmission to balance among the nodes, without generating load pressure problem.
· provide hierarchical protection for application systems in terms of importance
TxCloud importance core application system should have disaster tolerance. When the application system is interrupted by accident, it can have the corresponding disaster tolerant server, and continue to provide service to the outside world.
· The "physical + virtual" environment is complex and requires data protection products to provide a unified solution
TxCloud integrates all the protected objects in the user's IT environment, including physical machines and virtualization platforms, into a unified protection scheme through the central node of the system, providing a unified and simple management mode.
· The operation and maintenance management mode is unified, simple and efficient
TxCloud provides a unified and efficient management mode through the All-in-One-Web management console, although the user's own many application systems, the environment is complex, but the data protection scheme has not become difficult to manage, but very efficient, very simple.







